Make Best Use Of Performance with Universal Cloud Storage Solution and Assistance
Make Best Use Of Performance with Universal Cloud Storage Solution and Assistance
Blog Article
Enhance Information Safety With Universal Cloud Storage Space
Universal cloud storage space provides a compelling option to reinforce data safety procedures with its durable functions and capacities. By using the power of security, gain access to controls, and catastrophe healing techniques, universal cloud storage not only safeguards delicate details but also ensures information accessibility and honesty.
Benefits of Universal Cloud Storage Space
Exploring the benefits of implementing Universal Cloud Storage exposes its performance in improving data security actions (linkdaddy universal cloud storage press release). Additionally, Universal Cloud Storage supplies scalability, allowing services to conveniently increase their storage capability as their data needs expand, without the requirement for substantial financial investments in infrastructure.
Additionally, Universal Cloud Storage boosts information safety with attributes such as encryption, gain access to controls, and automated back-ups. Encryption ensures that information is securely sent and kept, safeguarding it from unapproved accessibility. Accessibility controls allow companies to define who can access specific data, adding an added layer of security. Automated backups ensure that information is consistently backed up, minimizing the danger of information loss because of mishaps or cyber attacks.
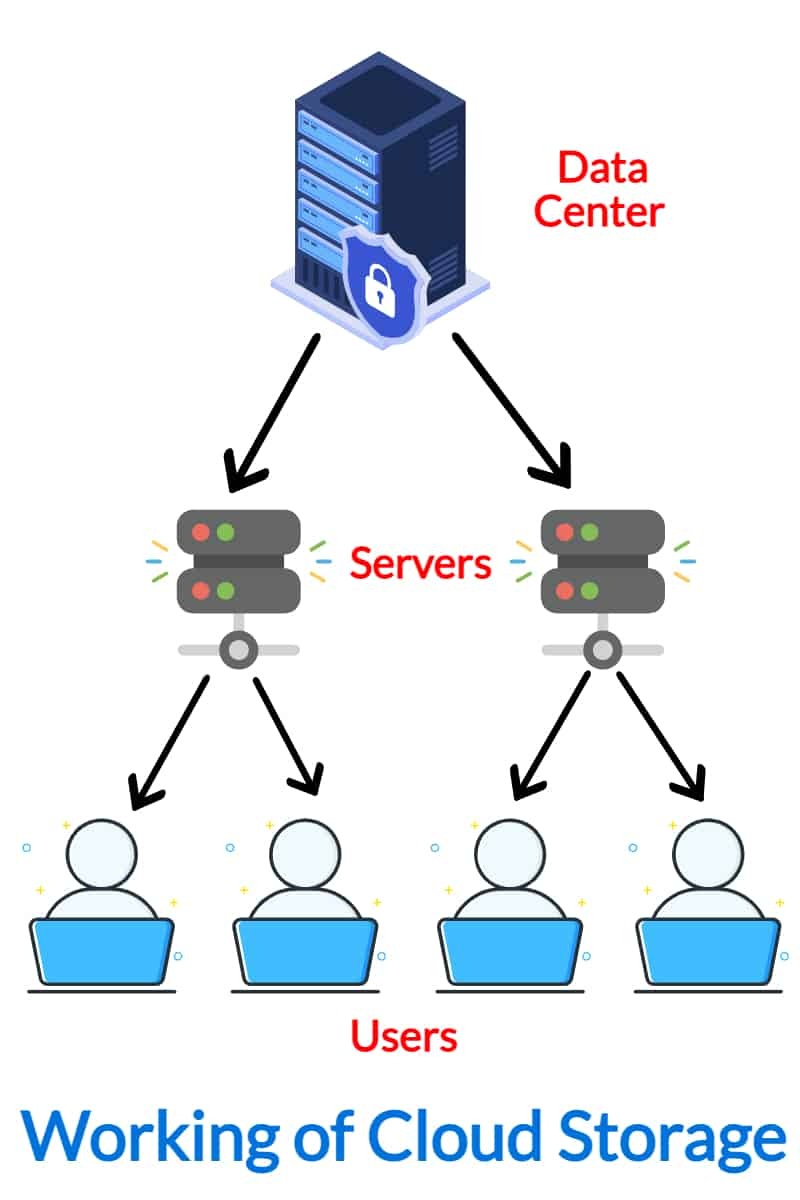
Key Functions for Information Security
Secret safety attributes play an important role in guarding information honesty and confidentiality within Universal Cloud Storage systems. Furthermore, regular data back-ups are important for avoiding information loss due to unexpected events like system failures or cyber-attacks.
Audit logs and activity monitoring enable organizations to track data access and alterations, aiding in the detection of any type of unauthorized actions. Generally, these crucial functions jointly contribute to robust data defense within Universal Cloud Storage space systems.
Implementing Secure Gain Access To Controls
Safe accessibility controls are crucial in ensuring the integrity and confidentiality of information within Universal Cloud Storage space systems. By carrying out protected gain access to controls, companies can manage that can see, customize, or remove information saved in the cloud. One fundamental element of safe access controls is verification. This process confirms the identity of users attempting to access the cloud storage system, stopping unauthorized individuals from acquiring access.
An additional critical element is consent, which determines the level of accessibility given to verified individuals. Role-based accessibility control (RBAC) is an usual technique that designates certain permissions based on the functions individuals have within the organization. Furthermore, implementing multi-factor verification adds an extra layer of this article safety by needing customers to offer multiple kinds of confirmation before accessing data.
Normal monitoring and auditing of gain access to controls are necessary to identify any type of dubious activities without delay. By continuously examining and improving access control plans, organizations can proactively guard their data from unauthorized gain access to or violations within Universal Cloud Storage space atmospheres.
Information Encryption Finest Practices
A durable data file encryption strategy is necessary for boosting the safety of info stored in Universal Cloud Storage space systems. Information security ideal practices include encrypting data both en route and at remainder. When data is in transit, making use of safe and secure interaction procedures such as SSL/TLS makes sure that details traded between the customer and the cloud storage is encrypted, stopping unauthorized accessibility. At rest, information need to be secured using solid file encryption formulas to shield it from being compromised if the storage space framework is breached.
Secret administration is one more crucial aspect of information encryption best methods. Implementing proper key management procedures makes certain that security secrets are securely stored and handled, preventing unapproved access to the encrypted data. On a regular basis upgrading encryption keys and revolving them go to the website helps improve the protection of the data gradually.

Backup and Calamity Recuperation Approaches
To make sure the continuity of procedures and safeguard against information loss, companies must establish robust back-up and catastrophe recuperation techniques within their Universal Cloud Storage space systems. In case of information corruption, accidental removal, or a cyber attack, having reputable back-ups is vital for restoring shed info quickly. Back-up methods must include regular automated backups of vital information to multiple locations within the cloud to minimize the danger of data loss. It is advisable to carry out a mix of complete backups and incremental back-ups to optimize storage area and minimize recovery time. Catastrophe recuperation plans should detail procedures for bring back information and applications in situation of a disastrous occasion that influences the main cloud storage. Testing these methods occasionally is important to ensure their performance and identify any potential voids in the recuperation procedure. By carrying out detailed back-up and calamity recovery methods, companies can improve the durability of their information monitoring practices and minimize the impact of unforeseen data cases.
Verdict
Finally, universal cloud storage space provides a durable option for enhancing information safety and security via functions like encryption, accessibility controls, and backup strategies. By carrying out protected accessibility controls and complying with data file encryption best methods, organizations can successfully safeguard delicate information from unapproved access and stop data loss. Back-up and calamity healing strategies additionally enhance information safety steps, ensuring information integrity and Going Here schedule in the occasion of unexpected incidents.
Report this page